Hi,
Please find the key for June 2011 question paper. Please leave a comment if you find any wrong answers.
Download the question paper here
1. Any integer composed of 3 POW n identical digits divisible by
(A) 2 POW n (B) 3 POW n
(C) 5 POW n (D) 7 POW n
Answer: (D)
************************************************************************
(9) A multiplexer is a logic circuit that
(A) accepts one input and gives several output
(B) accepts many inputs and gives many output
(C) accepts many inputs and gives one output
(D) accepts one input and gives one output
Answer: (C)
************************************************************************
(10) 8-bit 1’s complement form of –77.25 is
(A) 01001101.0100
(B) 01001101.0010
(C) 10110010.1011
(D) 10110010.1101
Solution: convert 77 into binary . i.e.. 01001101
convert 0.25 into binary. i.e.. 0100
binary equivalent of 77.25 = 01001101.0100
make 1's into 0's and 0's into 1's = 10110010.1011
Answer:(C)
************************************************************************
(11) From the point of view of the programmer, what are the major advantages of using a high-level
language rather than internal machine code or assembly language ?
(A) Program portability
(B) Easy development
(C) Efficiency
(D) None of the above
Answer: (B)
************************************************************************
(12) What features make C++ so powerful ?
(A) Easy implementation
(B) Reusing old code
(C) Easy memory management
(D) All of the above
Answer: (D)
************************************************************************
(13) The goal of operator overloading is
(A) to help the user of a class
(B) to help the developer of a class
(C) to help define friend function
(D) None of the above
Answer: (A)
************************************************************************
(14) The scheme of which interpreter translates the source program is known as
(A) Paragraph by paragraph
(B) Instruction by instruction
(C) Line by line
(D) None of the above
Answer: (C)
************************************************************************
(15) Portable program means
(A) Program with wheels
(B) Independent from its authors
(C) Independent of platform
(D) None of the above
Answer: (C)
************************************************************************
(16) Which of the following is the recovery management technique in DDBMS ?
(A) 2PC (Two Phase Commit)
(B) Backup
(C) Immediate update
(D) All of the above
Answer: (A)
************************************************************************
(17) Which of the following is the process by which a user’s privileges ascertained ?
(A) Authorization
(B) Authentication
(C) Access Control
(D) None of these
Answer: (C)
************************************************************************
(18) The basic variants of time-stampbased method of concurrency control are
(A) Total time stamp-ordering
(B) Partial time stamp ordering
(C) Multiversion Time stamp ordering
(D) All of the above
Answer: (D)
************************************************************************
19. A transaction can include following basic database access operations :
(A) Read_item(X)
(B) Write_item(X)
(C) Both (A) and (B)
(D) None of these
Answer: (C)
************************************************************************
(20) Decomposition help in eliminating some of the problems of bad design
(A) Redundancy
(B) Inconsistencies
(C) Anomalies
(D) All of the above
Answer: (D)
************************************************************************
21. The number of different trees with 8 nodes is
(A) 256
(B) 255
(C) 248
(D) None of these
Answer: (D)
************************************************************************
(22) Given a binary tree whose inorder and preorder traversal are given by
Inorder : EICFBGDJHK
Preorder : BCEIFDGHJK
The post order traversal of the above binary tree is
(A) I E FCGJ KHDB
(B) I E FC J GKHDB
(C) I E FCGKJ HDB
(D) I E FCGJ KDBH
Answer:(A)
************************************************************************
(23) The number of disk accesses performed by insertion operation in B-tree of height h is
(A) 0(1)
(B) 0(1gh)
(C) 0(h)
(D) None of these
Answer:(C)
************************************************************************
24. Consider a hash table of size m = 10000 and the hash function
h(k) = m (kA mod 1) for A =ROOT ( 5 – 1) / 2 . The location to the key k = 123456 is
(A) 46 (B) 47
(C) 41 (D) 43
Answer:(C)
************************************************************************
25. When the priority queue is represented by max heap, the insertion and deletion of an element
can be performed in (queue containing n elements)
(A) q(n) and q(1) respectively
(B) q(n) and q(n) respectively
(C) q(1) and q(1) respectively
(D) None of the above
Answer:(D)
************************************************************************
26. A comparison of frequency division and time division multiplexing system shows that
(A) FDM requires a lower bandwidth, but TDM has greater noise immunity.
(B) FDM has greater noise immunity and requires lower bandwidth than TDM.
(C) FDM requires channel synchronization, while TDM has greater noise immunity.
(D) FDM requires more multiplex while TDM requires band pass filter.
Answer:(C)
************************************************************************
(27) If carrier modulated by a digital bit stream, has one one of the possible phase of 0, 90, 180 and 270 degrees, then modulation called
(A) BPSK (B) QPSK
(C) QAM (D) MSK
Answer:(B)
************************************************************************
28. Consider the following statement :
(i) The bandwidth of the A.M., wave depends on the band width of the modulating signal.
(ii) The bandwidth of the A.M., wave depends on the modulation index.
(iii) The bandwidth of the F.M, wave for all practical purpose depends on the amplitude of the carrier.
Of these statements the correct statements are
(A) (i, ii)
(B) (i, iii)
(C) (ii, iii)
(D) All of the above
Answer:(A)
************************************************************************
29. A smart modem can dial, hangup and answer incoming calls automatically. Can you tell who
provides the appropriate instructions to the modem for this purpose ?
(A) Communication software
(B) Error detection protocols
(C) Link access procedure (LAP)
(D) Telecommunications
Answer:(D)
************************************************************************
(30) Which of the following switching techniques is most suitable for interactive traffic ?
(A) Circuit switching
(B) Message switching
(C) Packet switching
(D) All of the above
Answer:(C)
************************************************************************
31. Object modules generated by assembler that contains unresolved external references are resolved for
two or more object module by a/an
(A) Operating system
(B) Loader
(C) Linker
(D) Compiler
Answer:(C)
************************************************************************
32. A special software that is used to create a job queue is called
(A) Drive
(B) Spooler
(C) Interpreter
(D) Linkage editor
Answer:(B)
************************************************************************
33. Which of the following permanent database that has an entry for each
terminal symbol ?
(A) Literal table
(B) Identifier table
(C) Terminal table
(D) Source table
Answer:(C)
************************************************************************
(34) In which way(s) a macroprocessor for assembly language can be implemented ?
(A) Independent two-pass processor
(B) Independent one-pass processor
(C) Expand macrocalls and
substitute arguments
(D) All of the above
Answer:(D)
************************************************************************
35. Which of the following can be accessed by transfer vector approach of linking ?
(A) External data segments
(B) External subroutine
(C) Data located in other
procedure
(D) All of the above
Answer:(B)
************************************************************************
36. Block or Buffer caches are used to
(A) improve disk performance
(B) handle interrupts
(C) increase the capacity of main memory
(D) speed up main memory Read operations
Answer:(D)
************************************************************************
37. A file organization component VSAM file is
(A) Relative records data set
(B) Keyed sequential data set
(C) Entry sequential data set
(D) All of the above
Answer:(B)
************************************************************************
(38) A relationship between processes such that each has some part (critical
section) which must not be executed while the critical section of another
is being executed, is known as
(A) Semaphore
(B) Mutual exclusion
(C) Multiprogramming
(D) Message passing
Answer:(B)
************************************************************************
39. How many states can a process be in ?
(A) 3 (B) 4
(C) 2 (D) 5
Answer:(D)
************************************************************************
40. Which command allows you to view your file 24 lines at a time ?
(A) More
(B) Cat
(C) Pg
(D) None of the above
Answer:(C)
************************************************************************
41. Which one of the items listed below is not one of the software engineering layers ?
(A) Process
(B) Manufacturing
(C) Method
(D) Tools
Answer:(B)
************************************************************************
42. What is the first stage in program development ?
(A) Specification and design
(B) System Analysis
(C) Testing
(D) None of the above
Answer:(D)
************************************************************************
43. By means of a data flow diagram, the analyst can detect
(A) Task duplication
(B) Unnecessary delays
(C) Task overlapping
(D) All of the above
Answer:(D)
************************************************************************
44. Which of these are the 5 generic software engineering framework activities ?
(A) Communication, planning, modelling, construction, deployment
(B) Communication, risk, management, measurement, production, reviewing
(C) Analysis, designing, programming, Debugging, maintenance
(D) Analysis, planning, designing, programming, testing
Answer:(A)
************************************************************************
45. Many causes of the software crisis can be traced to mythology based on
(A) Management Myths
(B) Customer Myths
(C) Practitioner Myths
(D) All of the above
Answer:(D)
************************************************************************
46. Data warehousing refers to
(A) storing data offline at a separate site
(B) backing up data regularly
(C) is related to data mining
(D) uses tape as opposed to disk
Answer:()
************************************************************************
47. Virtual memory is
(A) related to virtual reality
(B) a form of ROM
(C) a form of RAM
(D) None of the above
Answer:()
************************************************************************
48. “M-Commerce” refers to
(A) a myth which does not exist in reality
(B) the ability of business to reach potential customers wherever they are
(C) the ability to have large capacity of memory storage dealing trade and commerce
(D) None of the above
Answer:(D)
Wireless electronic commerce used for conducting commerce or business through a handy device like cellular phone or PDA's
************************************************************************
49. The principal electronic payment systems for electronic commerce is
(A) Credit Card
(B) Digital Wallet
(C) Electronic Cheque
(D) All of the above
Answer:(D)
************************************************************************
50. Which is the most valuable electronic commerce to the individual customer in long run ?
(A) Business to Customer
(B) Business to Business
(C) Customer to Customer
(D) None of the above
Answer:(A)
----------------------------------------------------------------------------------------------------------
Description:
UGC NET Solved Sample Question Paper, ugc net solved question papers 2008, ugc net guide, ugc net papers, ugc net, ugc india, ugc payscale, ugc 6th pay comission, ugc pay revission, ugc syllabus, ugc exam, ugc result, ugc pay calculator, ugc india, ugc india website, ugc india new pay scale, ugc education, ugc net result, ugc net 2009, ugc net 2008, ugc net result, ugc net question papers, ugc net december 2008, ugc net june 2008 result, ugc net application form, ugc net result, ugc net application, ugc net in computer science, ugc net in india,
tags:
net solved papers computer science, net computer science question paper , ugc net computer science solved papers, free net solved papers computer science, net computer science study material, net computer science books, net computer science syllabus, net solved papers for computer science, net solved papers 2011, net solved papers free download, June 2011 solved paper,apset 2012, apset previous question papers, apset computer science question papers, previous question papers,apset previous question papers,apset previous question papers 2012, apset previous question papers 2011, previous question papers of apset, apset syllabus, apset syllabus 2012, apset syllabus 2012 paper 1, syllabus for apset 2012, apset computer science model papers, apset computer science material, apset syllabus for computer science
-------------------------------------------------------------------------------------------------------------------------------------------------------------------
Please find the key for June 2011 question paper. Please leave a comment if you find any wrong answers.
Download the question paper here
1
|
2
|
3
|
4
|
5
|
6
|
7
|
8
|
9
|
10
|
|
1 to 10
|
B
|
A
|
A
|
C
|
B
|
B
|
A
|
D
|
C
|
C
|
11to20
|
B
|
D
|
A
|
C
|
C
|
A
|
C
|
D
|
C
|
D
|
21 to30
|
D
|
A
|
C
|
C
|
D
|
C
|
B
|
A
|
D
|
C
|
4
|
C
|
B
|
C
|
D
|
B
| D |
B
|
B
|
D
|
C
|
5
|
B
|
D
|
D
|
A
|
D
|
A
|
C
|
D
|
D
|
A
|
Explanation the key:
----------------------------------------------------------------------------------
1. Any integer composed of 3 POW n identical digits divisible by
(A) 2 POW n (B) 3 POW n
(C) 5 POW n (D) 7 POW n
Answer:
Let n=1 then take 111 as example number
Let n=1 then take 111 as example number
substitute n=1 in the options then
(A) 2
111 is not divisible by 2. so Option (A) is wrong answer
(B) 3
111 is divisible by 3. So option (B) may be correct answer
(C) 5
111 is not divisible by 5. so Option (C) is wrong answer
(D)7
111 is not divisible by 7. so Option (D) is wrong answer
So Option(B) is Correct answer
**********************************************************************
(2) The circumference of the two concentric disks are divided into 100 sections each. For the outer disk, 100 of the sections are painted red and 100 of the sections are painted blue. For the inner disk, the sections are painted red and blue in an arbitrary manner. It is possible to align the two disks so that
(A) 100 or more
(B) 125 or more
(C) 150 or more
(D) 175 or more
of the sections on the inner disks have their colours matched with the corresponding section on outer disk.
Answer: (A)
(A) 100 or more
(B) 125 or more
(C) 150 or more
(D) 175 or more
of the sections on the inner disks have their colours matched with the corresponding section on outer disk.
Answer: (A)
*********************************************************************
(3) The proposition ~ p V q is equivalent to
(A) p --> q
(B) q --> p
(C) p <--> q
(D) p V q
Answer: (A) p--> q = ~p V q
(A) p --> q
(B) q --> p
(C) p <--> q
(D) p V q
Answer: (A) p--> q = ~p V q
**********************************************************************
(4) The absorption law in Boolean algebra say that
(A) X + X = X
(B) X . X = X
(C) x + x . y = x
(D) None of the above
Answer: (C)
(A) X + X = X
(B) X . X = X
(C) x + x . y = x
(D) None of the above
Answer: (C)
Other boolean algebra laws
**********************************************************************
(5) The number of 1’s present in the binary representation of
10 × 256 + 5 × 16 + 5 is
(A) 5 (B) 6
(C) 7 (D) 8
10 * 256 + 5 * 16+ 5 = 2645
10 × 256 + 5 × 16 + 5 is
(A) 5 (B) 6
(C) 7 (D) 8
10 * 256 + 5 * 16+ 5 = 2645
convert 2645 into boolean by dividing with 2.
Answer: (B)
***********************************************************************
(6)The hexadecimal number equivalent to (1762.46)8 is
(A) 3F2.89
(B) 3F2.98
(C) 2F3.89
(D) 2F3.98
convert octal into binary form. convert each digit into triplet form
(A) 3F2.89
(B) 3F2.98
(C) 2F3.89
(D) 2F3.98
convert octal into binary form. convert each digit into triplet form
(1762.46) = 001111110010.100110
0011 1111 0010.1001 1000 = 3F2.98
Answer: (B)
Answer: (B)
************************************************************************
(7) (A + B) AB bar is equivalent to
(A) A XOR B
(B) A XNOR B
(C) (A XOR B) XNOR A
(D) (A XNOR B) XOR A
Answer: (A)
************************************************************************
(8) A latch is constructed using two cross-coupled
(A) AND and OR gates
(B) AND gates
(C) NAND and NOR gates
(D) NAND gates
(A) A XOR B
(B) A XNOR B
(C) (A XOR B) XNOR A
(D) (A XNOR B) XOR A
Answer: (A)
************************************************************************
(8) A latch is constructed using two cross-coupled
(A) AND and OR gates
(B) AND gates
(C) NAND and NOR gates
(D) NAND gates
Answer: (D)
************************************************************************
(9) A multiplexer is a logic circuit that
(A) accepts one input and gives several output
(B) accepts many inputs and gives many output
(C) accepts many inputs and gives one output
(D) accepts one input and gives one output
Answer: (C)
************************************************************************
(10) 8-bit 1’s complement form of –77.25 is
(A) 01001101.0100
(B) 01001101.0010
(C) 10110010.1011
(D) 10110010.1101
Solution: convert 77 into binary . i.e.. 01001101
convert 0.25 into binary. i.e.. 0100
binary equivalent of 77.25 = 01001101.0100
make 1's into 0's and 0's into 1's = 10110010.1011
Answer:(C)
************************************************************************
(11) From the point of view of the programmer, what are the major advantages of using a high-level
language rather than internal machine code or assembly language ?
(A) Program portability
(B) Easy development
(C) Efficiency
(D) None of the above
Answer: (B)
************************************************************************
(12) What features make C++ so powerful ?
(A) Easy implementation
(B) Reusing old code
(C) Easy memory management
(D) All of the above
Answer: (D)
************************************************************************
(13) The goal of operator overloading is
(A) to help the user of a class
(B) to help the developer of a class
(C) to help define friend function
(D) None of the above
Answer: (A)
************************************************************************
(14) The scheme of which interpreter translates the source program is known as
(A) Paragraph by paragraph
(B) Instruction by instruction
(C) Line by line
(D) None of the above
Answer: (C)
************************************************************************
(15) Portable program means
(A) Program with wheels
(B) Independent from its authors
(C) Independent of platform
(D) None of the above
Answer: (C)
************************************************************************
(16) Which of the following is the recovery management technique in DDBMS ?
(A) 2PC (Two Phase Commit)
(B) Backup
(C) Immediate update
(D) All of the above
Answer: (A)
************************************************************************
(17) Which of the following is the process by which a user’s privileges ascertained ?
(A) Authorization
(B) Authentication
(C) Access Control
(D) None of these
Answer: (C)
************************************************************************
(18) The basic variants of time-stampbased method of concurrency control are
(A) Total time stamp-ordering
(B) Partial time stamp ordering
(C) Multiversion Time stamp ordering
(D) All of the above
Answer: (D)
************************************************************************
19. A transaction can include following basic database access operations :
(A) Read_item(X)
(B) Write_item(X)
(C) Both (A) and (B)
(D) None of these
Answer: (C)
************************************************************************
(20) Decomposition help in eliminating some of the problems of bad design
(A) Redundancy
(B) Inconsistencies
(C) Anomalies
(D) All of the above
Answer: (D)
************************************************************************
21. The number of different trees with 8 nodes is
(A) 256
(B) 255
(C) 248
(D) None of these
Answer: (D)
************************************************************************
(22) Given a binary tree whose inorder and preorder traversal are given by
Inorder : EICFBGDJHK
Preorder : BCEIFDGHJK
The post order traversal of the above binary tree is
(A) I E FCGJ KHDB
(B) I E FC J GKHDB
(C) I E FCGKJ HDB
(D) I E FCGJ KDBH
Answer:(A)
************************************************************************
(23) The number of disk accesses performed by insertion operation in B-tree of height h is
(A) 0(1)
(B) 0(1gh)
(C) 0(h)
(D) None of these
Answer:(C)
************************************************************************
24. Consider a hash table of size m = 10000 and the hash function
h(k) = m (kA mod 1) for A =ROOT ( 5 – 1) / 2 . The location to the key k = 123456 is
(A) 46 (B) 47
(C) 41 (D) 43
Answer:(C)
************************************************************************
25. When the priority queue is represented by max heap, the insertion and deletion of an element
can be performed in (queue containing n elements)
(A) q(n) and q(1) respectively
(B) q(n) and q(n) respectively
(C) q(1) and q(1) respectively
(D) None of the above
Answer:(D)
************************************************************************
26. A comparison of frequency division and time division multiplexing system shows that
(A) FDM requires a lower bandwidth, but TDM has greater noise immunity.
(B) FDM has greater noise immunity and requires lower bandwidth than TDM.
(C) FDM requires channel synchronization, while TDM has greater noise immunity.
(D) FDM requires more multiplex while TDM requires band pass filter.
Answer:(C)
************************************************************************
(27) If carrier modulated by a digital bit stream, has one one of the possible phase of 0, 90, 180 and 270 degrees, then modulation called
(A) BPSK (B) QPSK
(C) QAM (D) MSK
Answer:(B)
************************************************************************
28. Consider the following statement :
(i) The bandwidth of the A.M., wave depends on the band width of the modulating signal.
(ii) The bandwidth of the A.M., wave depends on the modulation index.
(iii) The bandwidth of the F.M, wave for all practical purpose depends on the amplitude of the carrier.
Of these statements the correct statements are
(A) (i, ii)
(B) (i, iii)
(C) (ii, iii)
(D) All of the above
Answer:(A)
************************************************************************
29. A smart modem can dial, hangup and answer incoming calls automatically. Can you tell who
provides the appropriate instructions to the modem for this purpose ?
(A) Communication software
(B) Error detection protocols
(C) Link access procedure (LAP)
(D) Telecommunications
Answer:(D)
************************************************************************
(30) Which of the following switching techniques is most suitable for interactive traffic ?
(A) Circuit switching
(B) Message switching
(C) Packet switching
(D) All of the above
Answer:(C)
************************************************************************
31. Object modules generated by assembler that contains unresolved external references are resolved for
two or more object module by a/an
(A) Operating system
(B) Loader
(C) Linker
(D) Compiler
Answer:(C)
************************************************************************
32. A special software that is used to create a job queue is called
(A) Drive
(B) Spooler
(C) Interpreter
(D) Linkage editor
Answer:(B)
************************************************************************
33. Which of the following permanent database that has an entry for each
terminal symbol ?
(A) Literal table
(B) Identifier table
(C) Terminal table
(D) Source table
Answer:(C)
************************************************************************
(34) In which way(s) a macroprocessor for assembly language can be implemented ?
(A) Independent two-pass processor
(B) Independent one-pass processor
(C) Expand macrocalls and
substitute arguments
(D) All of the above
Answer:(D)
************************************************************************
35. Which of the following can be accessed by transfer vector approach of linking ?
(A) External data segments
(B) External subroutine
(C) Data located in other
procedure
(D) All of the above
Answer:(B)
************************************************************************
36. Block or Buffer caches are used to
(A) improve disk performance
(B) handle interrupts
(C) increase the capacity of main memory
(D) speed up main memory Read operations
Answer:(D)
************************************************************************
37. A file organization component VSAM file is
(A) Relative records data set
(B) Keyed sequential data set
(C) Entry sequential data set
(D) All of the above
Answer:(B)
************************************************************************
(38) A relationship between processes such that each has some part (critical
section) which must not be executed while the critical section of another
is being executed, is known as
(A) Semaphore
(B) Mutual exclusion
(C) Multiprogramming
(D) Message passing
Answer:(B)
************************************************************************
39. How many states can a process be in ?
(A) 3 (B) 4
(C) 2 (D) 5
Answer:(D)
************************************************************************
40. Which command allows you to view your file 24 lines at a time ?
(A) More
(B) Cat
(C) Pg
(D) None of the above
Answer:(C)
************************************************************************
41. Which one of the items listed below is not one of the software engineering layers ?
(A) Process
(B) Manufacturing
(C) Method
(D) Tools
Answer:(B)
************************************************************************
42. What is the first stage in program development ?
(A) Specification and design
(B) System Analysis
(C) Testing
(D) None of the above
Answer:(D)
************************************************************************
43. By means of a data flow diagram, the analyst can detect
(A) Task duplication
(B) Unnecessary delays
(C) Task overlapping
(D) All of the above
Answer:(D)
************************************************************************
44. Which of these are the 5 generic software engineering framework activities ?
(A) Communication, planning, modelling, construction, deployment
(B) Communication, risk, management, measurement, production, reviewing
(C) Analysis, designing, programming, Debugging, maintenance
(D) Analysis, planning, designing, programming, testing
Answer:(A)
************************************************************************
45. Many causes of the software crisis can be traced to mythology based on
(A) Management Myths
(B) Customer Myths
(C) Practitioner Myths
(D) All of the above
Answer:(D)
************************************************************************
46. Data warehousing refers to
(A) storing data offline at a separate site
(B) backing up data regularly
(C) is related to data mining
(D) uses tape as opposed to disk
Answer:()
************************************************************************
47. Virtual memory is
(A) related to virtual reality
(B) a form of ROM
(C) a form of RAM
(D) None of the above
Answer:()
************************************************************************
48. “M-Commerce” refers to
(A) a myth which does not exist in reality
(B) the ability of business to reach potential customers wherever they are
(C) the ability to have large capacity of memory storage dealing trade and commerce
(D) None of the above
Answer:(D)
Wireless electronic commerce used for conducting commerce or business through a handy device like cellular phone or PDA's
************************************************************************
49. The principal electronic payment systems for electronic commerce is
(A) Credit Card
(B) Digital Wallet
(C) Electronic Cheque
(D) All of the above
Answer:(D)
************************************************************************
50. Which is the most valuable electronic commerce to the individual customer in long run ?
(A) Business to Customer
(B) Business to Business
(C) Customer to Customer
(D) None of the above
Answer:(A)
----------------------------------------------------------------------------------------------------------
Description:
UGC NET Solved Sample Question Paper, ugc net solved question papers 2008, ugc net guide, ugc net papers, ugc net, ugc india, ugc payscale, ugc 6th pay comission, ugc pay revission, ugc syllabus, ugc exam, ugc result, ugc pay calculator, ugc india, ugc india website, ugc india new pay scale, ugc education, ugc net result, ugc net 2009, ugc net 2008, ugc net result, ugc net question papers, ugc net december 2008, ugc net june 2008 result, ugc net application form, ugc net result, ugc net application, ugc net in computer science, ugc net in india,
tags:
net solved papers computer science, net computer science question paper , ugc net computer science solved papers, free net solved papers computer science, net computer science study material, net computer science books, net computer science syllabus, net solved papers for computer science, net solved papers 2011, net solved papers free download, June 2011 solved paper,apset 2012, apset previous question papers, apset computer science question papers, previous question papers,apset previous question papers,apset previous question papers 2012, apset previous question papers 2011, previous question papers of apset, apset syllabus, apset syllabus 2012, apset syllabus 2012 paper 1, syllabus for apset 2012, apset computer science model papers, apset computer science material, apset syllabus for computer science
-------------------------------------------------------------------------------------------------------------------------------------------------------------------
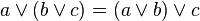

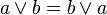
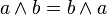
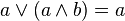

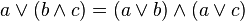




A comparison of frequency division and time division multiplexing system shows that
ReplyDelete(A) FDM requires a lower bandwidth, but TDM has greater noise immunity.
(B) FDM has greater noise immunity and requires lower bandwidth than TDM.
(C) FDM requires channel synchronization, while TDM has greater noise immunity.
(D) FDM requires more multiplex while TDM requires band pass filter.
Answer is (C)
Thanks a lot mini.... i would be thankful to you if you check other answers also....
ReplyDeletehow to convert .decimal to binary
ReplyDeletecan you explain
Thanks for providing the solutions, please check the necessaru correction in following questions
ReplyDelete(16) Which of the following is the recovery management technique in DDBMS ?
(A) 2PC (Two Phase Commit)
(B) Backup
(C) Immediate update
(D) All of the above
goto link and verify the answer
www.scribd.com/doc/55754397/2006
(14) The scheme of which interpreter translates the source program is known as
(A) Paragraph by paragraph
(B) Instruction by instruction
(C) Line by line
(D) None of the above
Ans B is more appropriate because there may be more than one instruction in a line.... please provide the details about this also.
Answer for question no 29 is communication software refer site http://lib.ru/unixhelp/mode.txt
ReplyDeleteVery nice post. I just stumbled upon your blog and wished to say that I've truly enjoyed browsing your blog posts. In any case I will be subscribing to your feed and I hope you write again very soon!
ReplyDeleteHere is my homepage :: Binary options trading signals